Full Disclosure of CVE-2022-0072, CVE-2022-0073, and CVE-2022-0074 and What You Should Do

Security has always been at the forefront of our development process at LiteSpeed Technologies. So when a vulnerability is discovered, we act quickly. Our priority is to empower our customers to better protect their systems, but we also take such situations as learning opportunities.
Today, as a part of that commitment, we want to share details of certain bugs reported in OpenLiteSpeed (OLS) and LiteSpeed Enterprise (LSWS) web servers.
Summary
- Three vulnerabilities were reported to LiteSpeed. These were fixed in OpenLiteSpeed v1.7.16 Build 1 and LiteSpeed Enterprise v6.0.12 Build 10.
- These vulnerabilities don’t impact the majority of our clients. One is within the Docker system, and the other two cannot be exploited without WebAdmin access.
- You should upgrade to the latest version and build of OpenLiteSpeed or LiteSpeed Enterprise, as appropriate.
- Future security updates will be released with incremented version numbers, and will no longer be released as new builds of existing version numbers.
About the Vulnerabilities
We would like to thank the Unit 42 Team at Palo Alto Networks for responsibly disclosing security issues in our OpenLiteSpeed and LiteSpeed Enterprise web servers on October 4th, and maintaining good communication throughout.
LiteSpeed’s Team acted swiftly and informed Unit 42 that the issues were under remediation.
On October 8th, we internally remediated these bugs and put them into testing. During this period we monitored the changes and ensured they were not affecting anything else.
On October 12th, we pushed the related updates to LiteSpeed Enterprise v6.0.12 as Build 10
On October 18th, we pushed the related updates to OpenLiteSpeed v1.7.16 as Build 1
On October 20th, our Docker Images for both OLS and LSWS were updated.
The reported vulnerabilities have the following CVE numbers: CVE-2022-0072, CVE-2022-0073 and CVE-2022-0074.
Palo Alto Networks has already released information about these CVEs, but we would like to expand on this, below.
CVE-2022-0072
Directory Traversal (CVE-2022-0072) rated Medium severity (CVSS 5.8)
[This issue] was a directory traversal vulnerability that could allow an attacker to bypass security measures and access forbidden files. An attacker that compromised the server could create a secret backdoor and exploit the vulnerability to access it.
This vulnerability applies to OpenLiteSpeed and LiteSpeed Enterprise WebAdmin Console, and is only exploitable after WebAdmin Authentication has been achieved.
Additionally, you must have root privileges in order to upload a custom exploit under /usr/local/lsws/admin/html.
CVE-2022-0073
Remote Code Execution (CVE-2022-0073) rated High severity (CVSS 8.8)
At the first stage of the attack, we tried to gain remote code execution and found that the OpenLiteSpeed Web Server admin dashboard is vulnerable to a command injection vulnerability. A threat actor who managed to gain the credentials to the dashboard, whether by brute force attacks or social engineering, could exploit the vulnerability in order to execute code on the server.
This also applies only to the OLS and LSWS WebAdmin Console for an authenticated user.
CVE-2022-0074
Privilege Escalation (CVE-2022-0074) rated High severity (CVSS 8.8)
While exploring the OpenLiteSpeed Docker image as
nobody, we found a misconfiguration in thePATHenvironment variable that could be exploited into a privilege escalation using the CWE untrusted search path.
This is another vulnerability that requires OpenLiteSpeed WebAdmin access in order to exploit. LiteSpeed Enterprise is not affected.
We were unable to reproduce this scenario in our tests with a standard real-world Docker installation. It seems that the environment used by the reporting team differs from the default Docker configuration. The reporting team’s /usr/local/bin folder was owned by the nobody user, which allowed the vulnerability to operate.
We tried to reproduce this bug on an Ubuntu 22 system with the default Docker host environment and the vulnerable build of our Docker image. We found that the /usr/local/bin directory was owned by root, and any attempt to change the files in the reported directory failed.
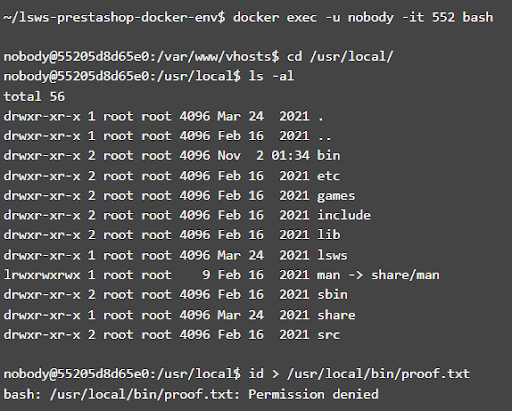
We don’t expect this vulnerability to impact standard Docker installations, however, we are in touch with the PaloAlto Networks Team to get more details on their Docker environment. We’d like to understand how it was customized to make this vulnerability possible.
Regardless, this is not a privilege escalation from within any LiteSpeed products.
What You Should Do
For Docker users, if you’re able to change the contents of /usr/local/bin in your environment, please update to our latest Docker image. An additional security layer which corrects the environment path will be added to your image, effectively patching any side-effects of this vulnerability.
We also recommend any manual web server installations to be updated by using the $LSWS_PATH/admin/misc/lsup.sh script. Installations installed via any RPM/package managers(yum/apt) will be updated automatically.
We always recommend, for your general security, that you do not share LiteSpeed WebAdmin authentication details with more than the necessary system administrators. We also suggest you set a strong password and take advantage of the available Brute Force protection available for WebAdmin.
For best-case scenarios, use a firewall to mask LiteSpeed WebAdmin Console from any public access.
We would like to once again thank the Unit 42 Team, for their help in making our products secure.

Comments